In today’s digital age, organizations are inundated with vast amounts of log data from multiple sources. However, managing this data effectively is challenging, especially with traditional methods that often create “log noise.” This makes it difficult for security teams to detect real threats and leaves organizations vulnerable to compliance and security risks. DeshCyber’s Splunk Turnkey Solution with syslog-ng is designed to solve these problems by offering a scalable, secure, and cost-effective way to manage log data for real-time insights.
What is syslog-ng, and Why is it Important for Log Management?
syslog-ng is a robust, open-source log management tool that collects, processes, and forwards log data from various sources into centralized systems like Splunk. It’s vital because it filters out irrelevant log data before it reaches the central storage, optimizing the log management process for better efficiency and cost savings.
Key Benefits of syslog-ng:
- Efficient Data Filtering: Filters out irrelevant data, reducing noise in the SIEM system.
- Improved Data Transformation: Ensures that logs are formatted and normalized to meet Splunk’s indexing requirements.
- Cost Savings: Fewer unnecessary logs mean lower storage and processing costs in Splunk.
DeshCyber’s Unique Splunk Turnkey Solution with syslog-ng
DeshCyber’s Splunk Turnkey Solution with syslog-ng provides an all-in-one package for seamless log management. Here’s what makes this solution unique and valuable:
- Comprehensive Implementation: DeshCyber handles every stage, from setting up syslog-ng to Splunk integration, making it a turnkey solution.
- Custom Filtering Rules: Customizable filters allow syslog-ng to capture only the logs necessary for security analysis.
- Scalability for Large Data Volumes: Built to handle growing data demands in organizations.
- Enhanced Compliance: Helps agencies meet security and regulatory requirements by retaining only necessary logs.
How We Deliver It
DeshCyber’s Splunk Turnkey Solution with syslog-ng offers an all-inclusive approach to streamlined, efficient log management. DeshCyber manages each stage—from configuring syslog-ng to integrating it with Splunk—delivering a true turnkey solution. This comprehensive setup allows organizations to benefit from custom filtering rules in syslog-ng, which capture only security-relevant logs. For instance, rather than overwhelming the SIEM system with all system logs, DeshCyber configures syslog-ng to retain only high-priority logs, such as unauthorized access attempts or unusual network activity. This selective filtering reduces log volume, cuts costs, and keeps Splunk focused on actionable data.
Built for scalability, this solution easily adapts to growing data volumes, making it suitable for large organizations and government agencies with evolving data demands. DeshCyber also enhances compliance by helping agencies meet regulatory requirements, retaining only necessary logs and ensuring data integrity. This unique solution keeps operations efficient, cost-effective, and secure.
How DeshCyber’s syslog-ng Solution Saves Costs

Log data can quickly inflate storage requirements, leading to high costs in a SIEM environment like Splunk. DeshCyber’s syslog-ng integration with Splunk reduces these costs in the following ways:
- Minimizing Data Volume: By filtering logs, syslog-ng reduces the amount of data forwarded to Splunk. This means lower storage costs.
- Reducing Processing Costs: With less data to analyze, Splunk’s processing resources are conserved, improving speed and reducing costs.
- Streamlined Compliance: By retaining only essential logs, syslog-ng helps organizations stay compliant with minimal storage impact
Reducing SIEM Noise with syslog-ng: Why It’s Essential
Noise in a SIEM system, like Splunk, refers to unnecessary or irrelevant logs that clutter the system. Excessive noise can lead to missed security threats and slow response times. DeshCyber’s syslog-ng filtering capabilities reduce SIEM noise by:
- Removing Routine System Logs: Filters out non-critical data such as routine health checks and operational logs.
- Streamlining Security Alerts: Allows Splunk to focus on real-time security threats rather than benign logs.
- Improving Threat Detection: With less clutter, security teams can respond faster to genuine alerts.
Technical Overview of DeshCyber’s syslog-ng Integration with Splunk
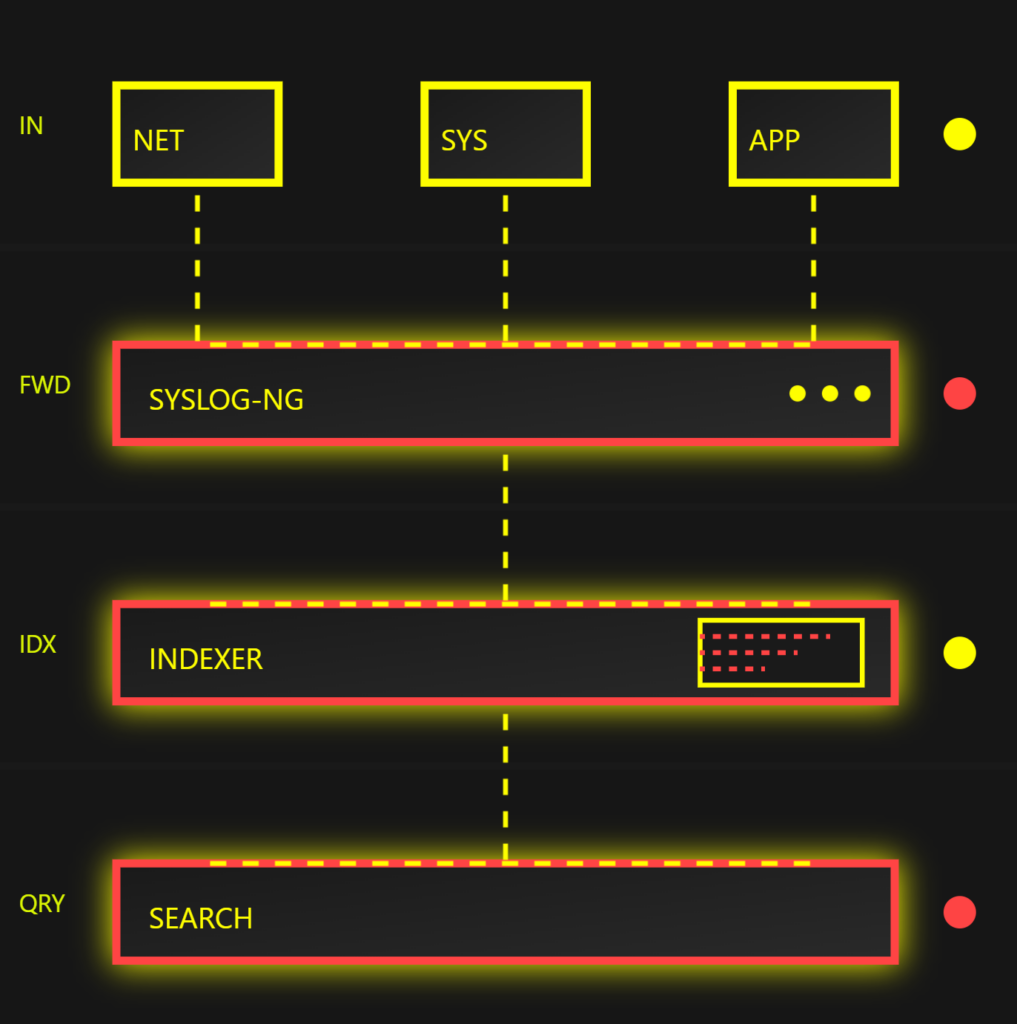
Step 1: Identifying Key Log Sources: DeshCyber works with organizations to identify critical sources like firewalls, databases, and application servers that generate high-priority logs.
Step 2: Configuring syslog-ng for Data Filtering: syslog-ng is configured to filter out unnecessary data. For instance, only critical logs such as unauthorized access attempts and anomaly detection are forwarded to Splunk.
Step 3: Ensuring Secure Log Transmission: DeshCyber configures syslog-ng to securely transmit logs, protecting data integrity during the transfer to Splunk.
Step 4: Data Normalization for Easy Analysis in Splunk: To facilitate search and reporting, syslog-ng normalizes log data before sending it to Splunk, ensuring consistency and accuracy.
